Microsoft Azure AD / Entra ID integration [C IG]
Overview
The AuthorisationService (AS) can integrate into a Microsoft Azure Active Directory (AAD, aka Microsoft Entra ID). Similar to the LDAP integration, AS will use KeyCloak to synchronize users and groups with AAD. Synchronized users and groups will also be generated in VidiCore.
The configuration is done in ConfigPortal in the Identity Provider configuration. ConfigPortal ensures that the appropriate configuration parameters are entered into KeyCloak.
The AS login screen was adapted to show a button to log in with Azure AD if it is configured. When the button is pressed, the user is forwarded to the AAD login page, including 2-factor authentication if enabled in the AAD.
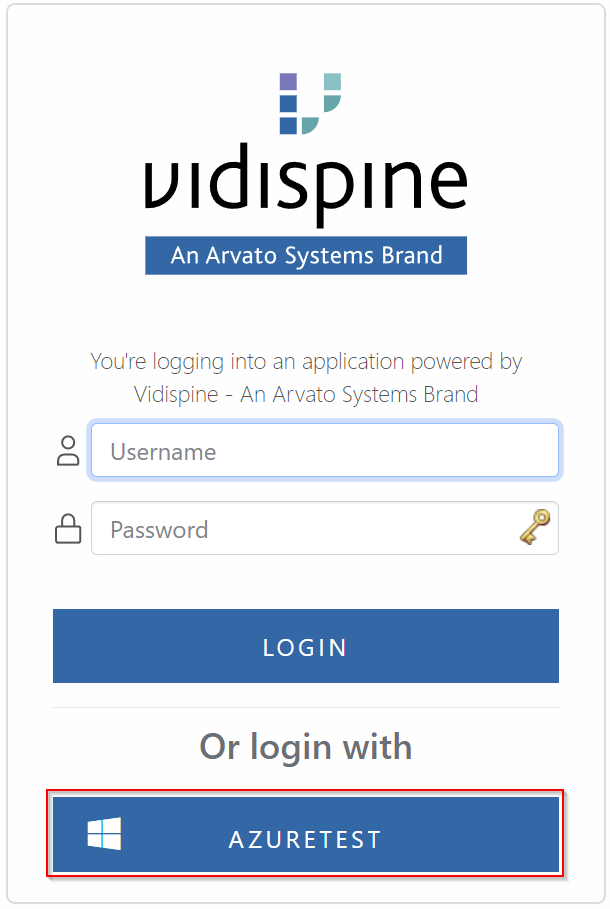
Change AS login screen with Azure AD login button
The synchronization between AAD and KeyCloak is regularly scheduled.
Configuration
AAD configuration
Several configuration steps have to be done in AAD before starting the integration:
Register new SAML application
The following link leads to a tutorial to register a new SAML application in Azure AD
https://learn.microsoft.com/en-us/azure/active-directory/saas-apps/saml-toolkit-tutorial
Create a SAML application from the Enterprise application following the steps from the screenshots:
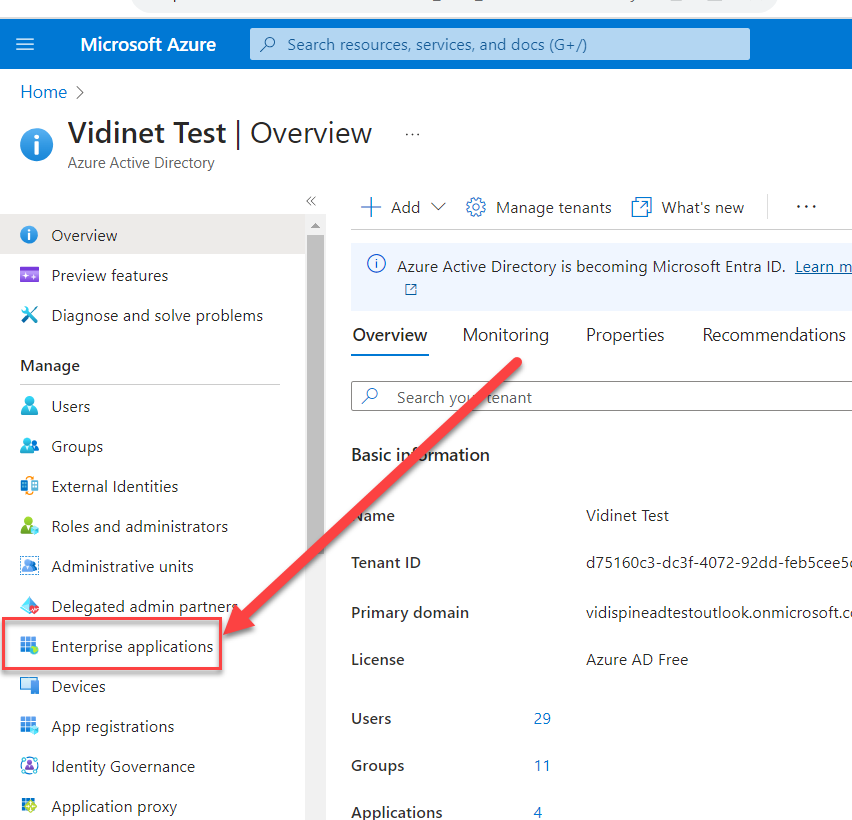
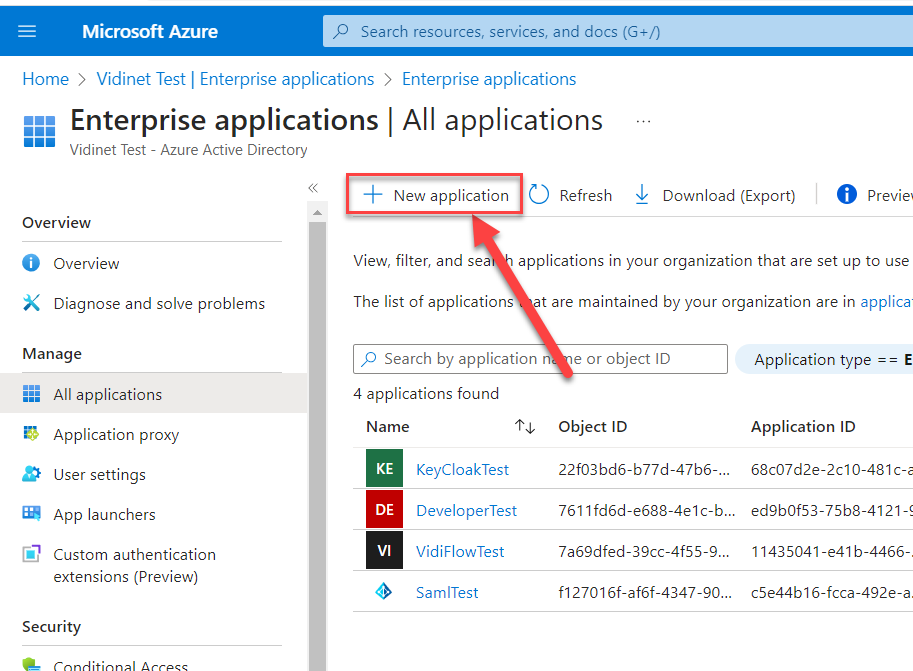
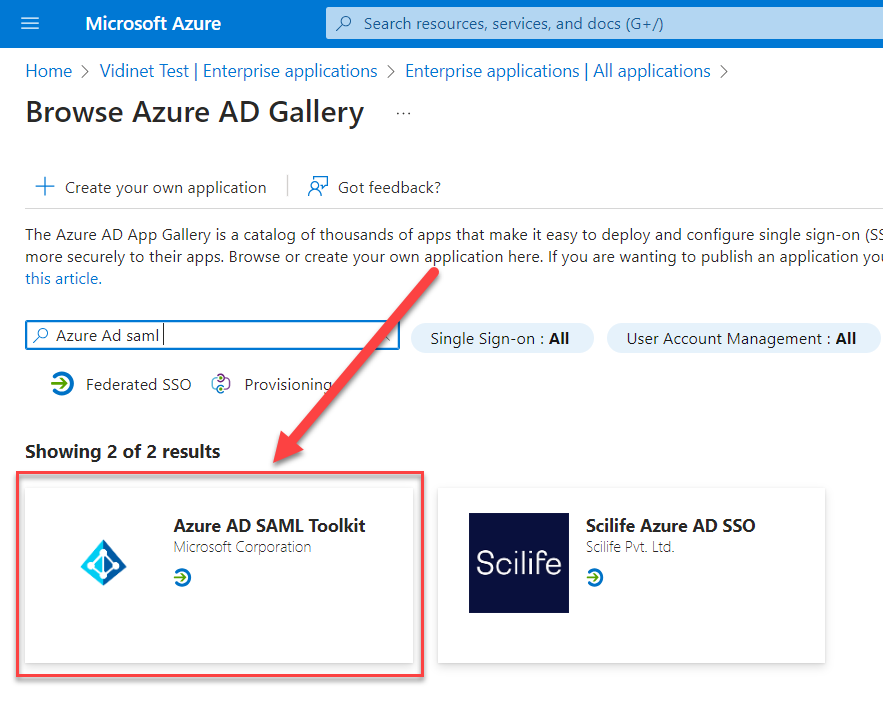
Enable Single sign-on
In the Enterprise Application, look for the Azure AD SAML service that has been created.
Go to manage → single sign-on and choose SAML as sign-on method.
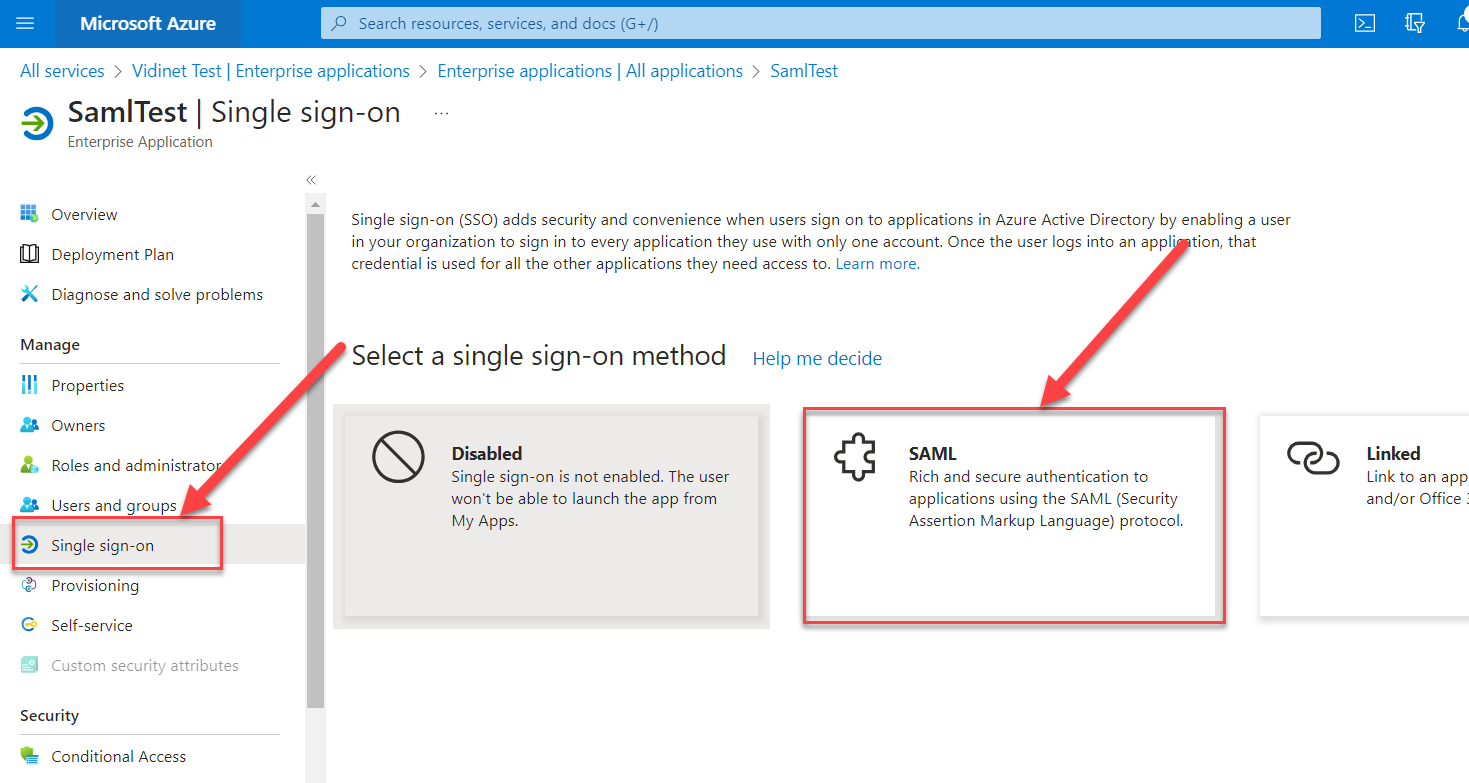
Configure the ‘Sign on URL’ using the AuthService endpoint
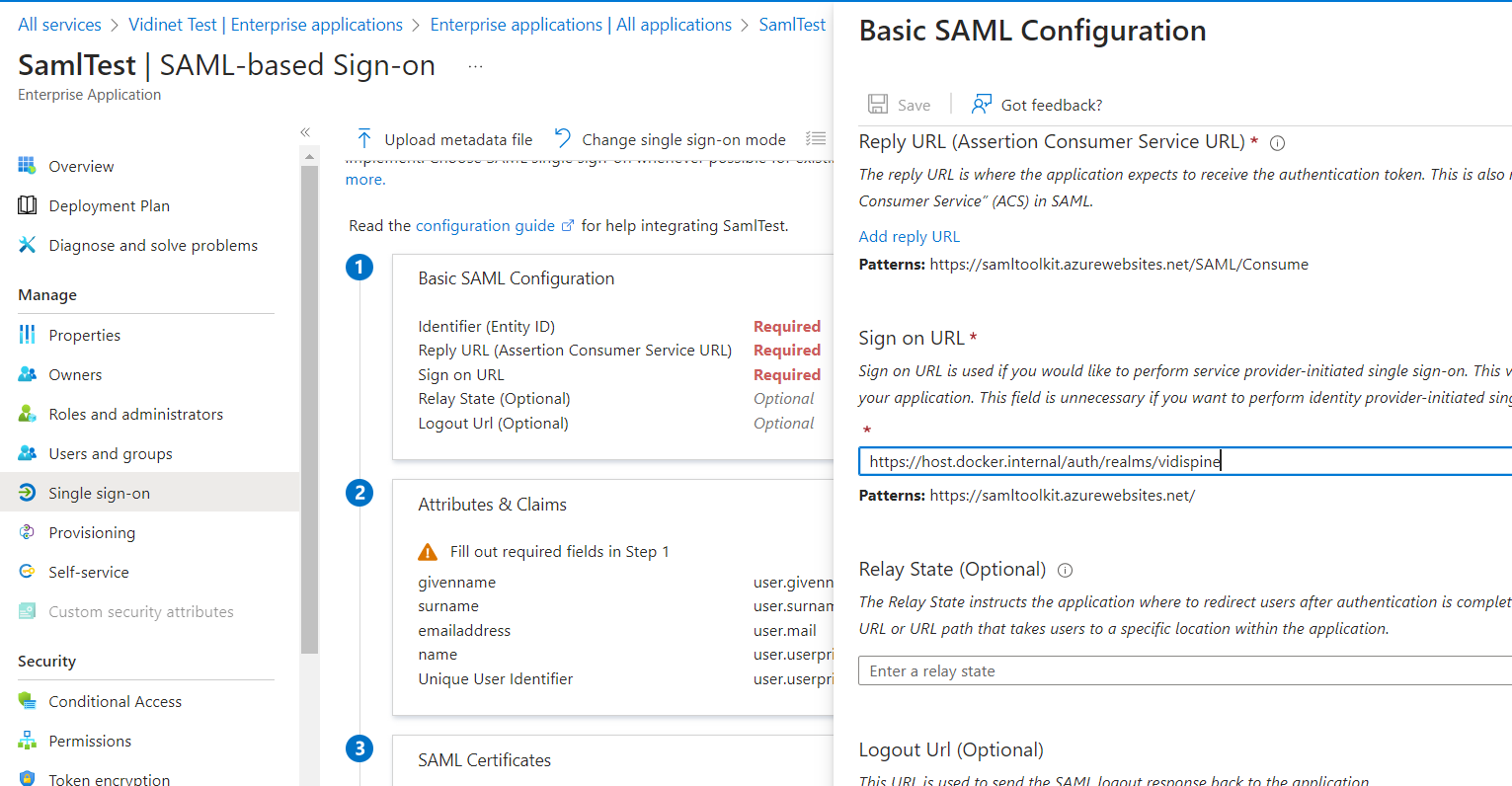
Get Client ID and Client Secret for SAML
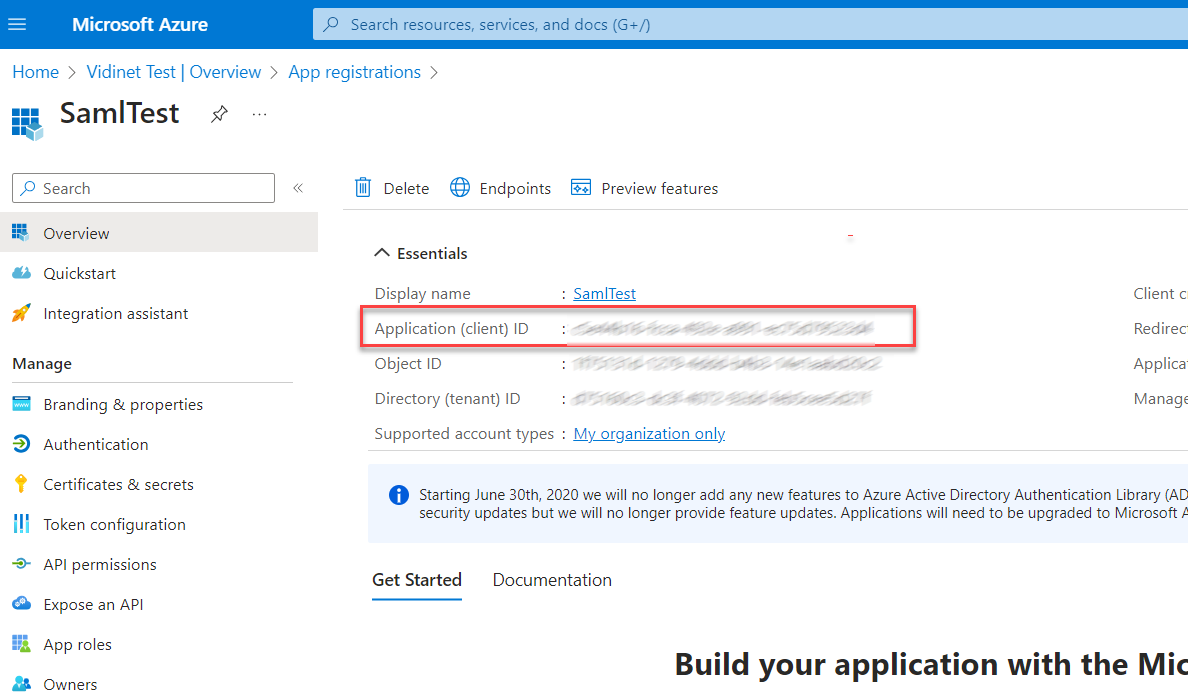
Get the Client ID from ‘Application (client) ID’
Create Client Secret from Certification & secrets
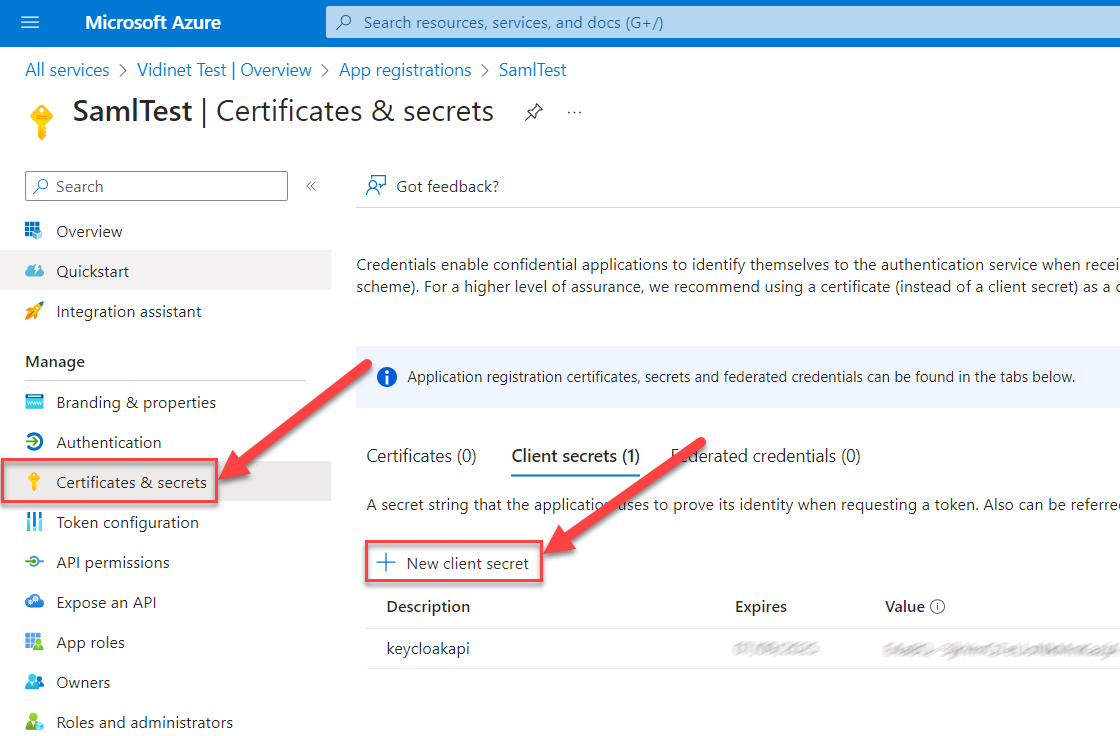
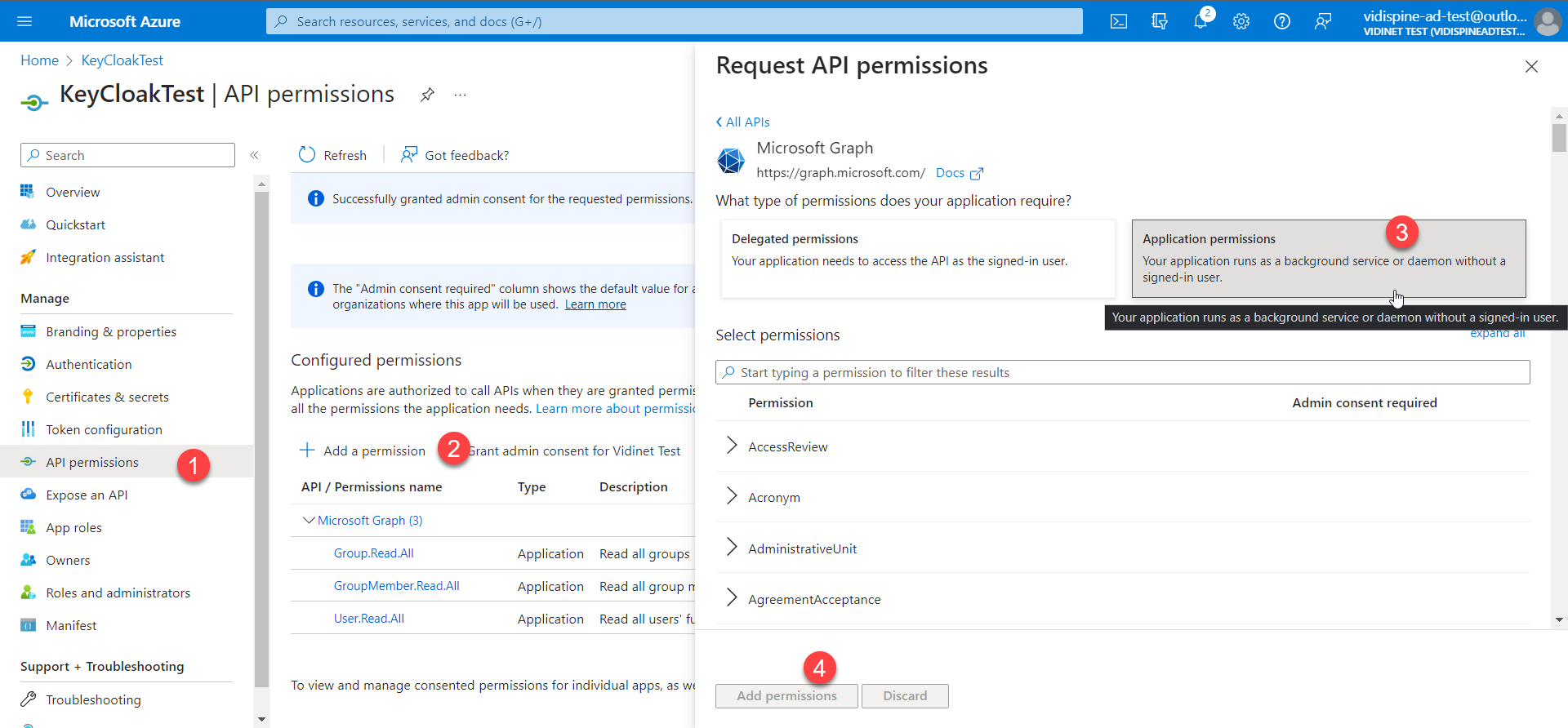
When registering the client within Azure Enterprise Applications, the following permissions are required by Keycloak’s Azure AD Provider plugin to be able to federate users and sync locally:
Group.Read.All
GroupMember.Read.All
User.Read.All
Create an Identity Provider in ConfigPortal
A new identity provider can be created in ConfigPortal
Go to Settings → Identity Provider → press + → Add Azure AD Configuration
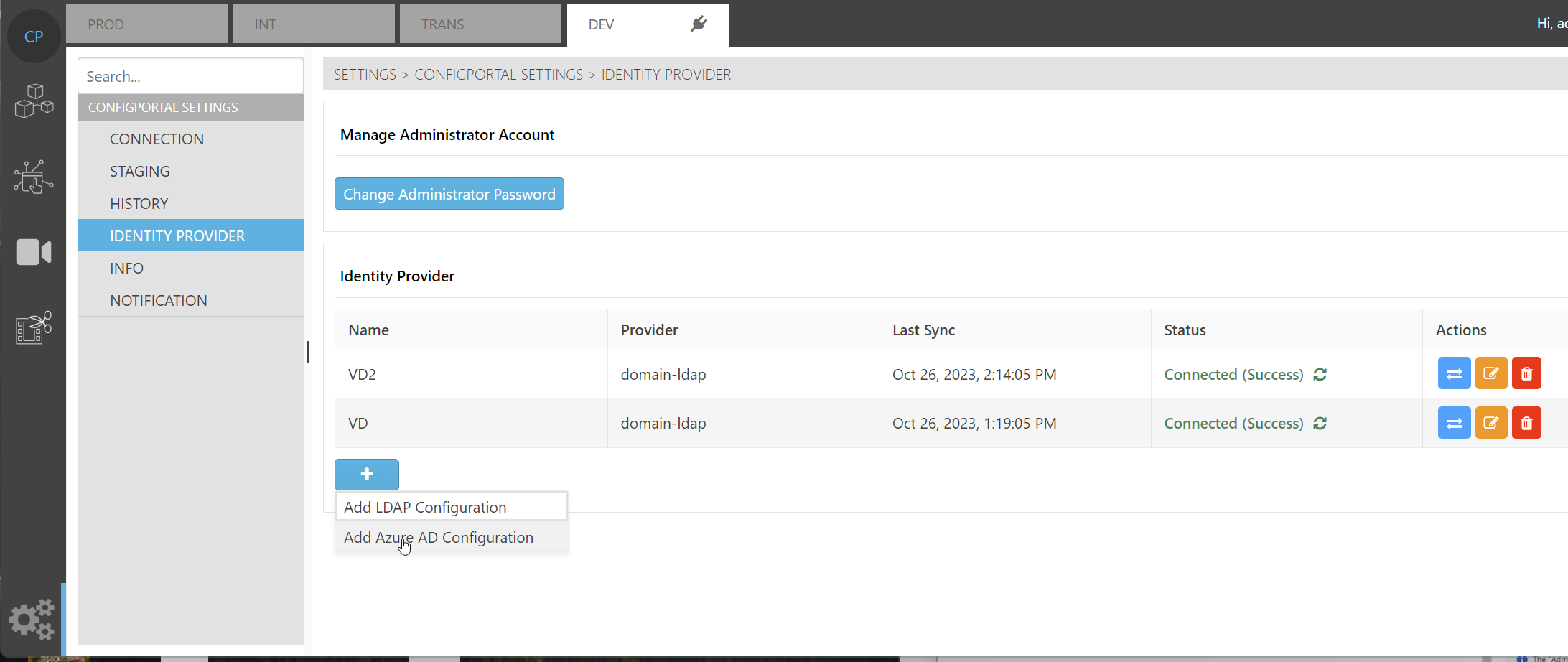
Create a new AAD Identity Provider in ConfigPortal
Fill out the dialog with the data from the AAD:
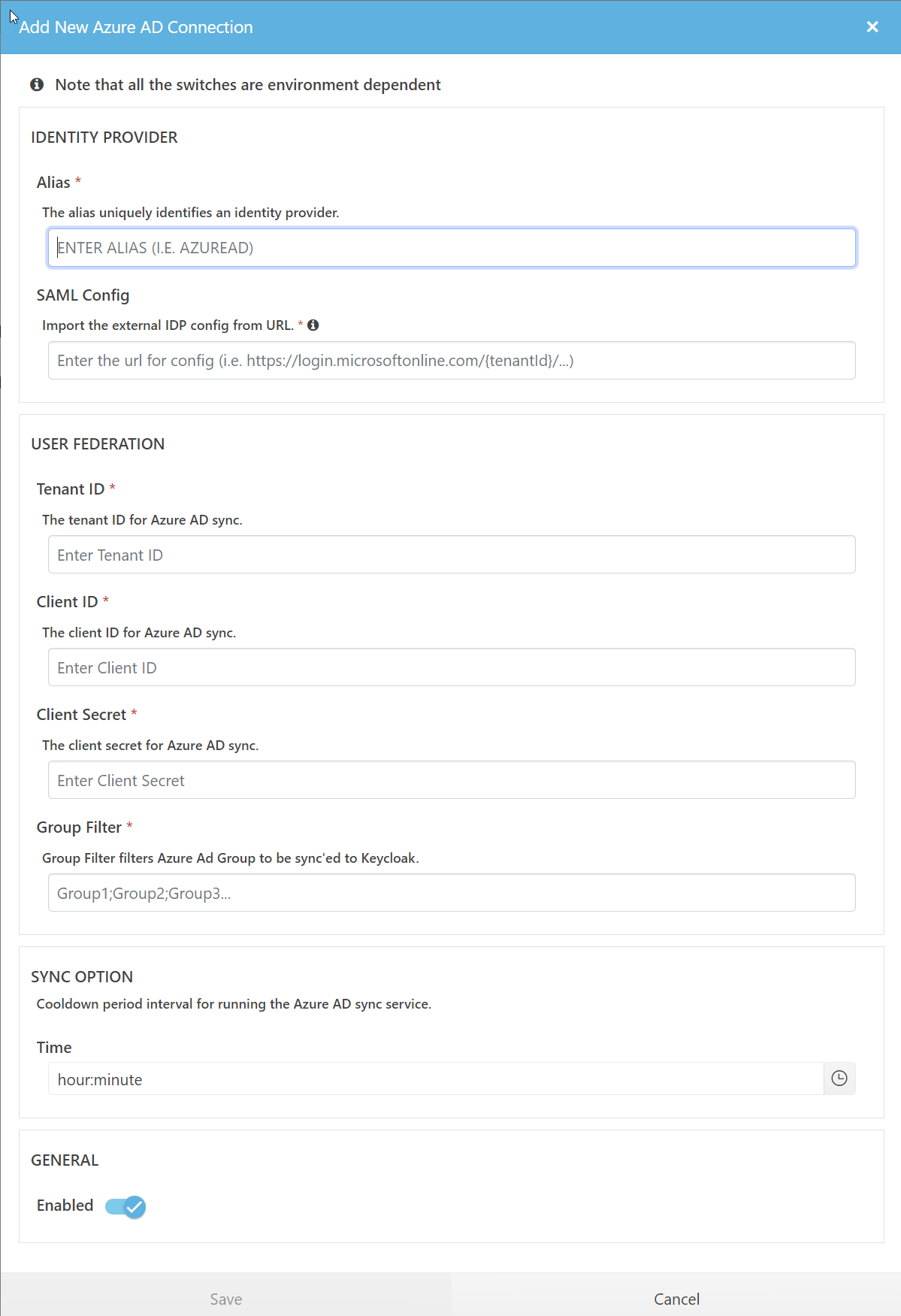
AAD Identity Provider configuration screen
The “Group Filter” allows to whitelist groups. Only users being member of at least one of these groups will be synced to KeyCloak and VidiCore. This feature can help to reduce the amount of users to be synced and for that reason speed up the sync process a lot.
Be aware that this feature will be enhanced in the future, probably without migration of the existing configuration.
Technical detail information
Microsoft Graph API
Microsoft Graph API is used for most of our enterprise app usages for retrieving data for user federation purpose in Keycloak.
Rest API: https://developer.microsoft.com/en-us/graph/graph-explorer/
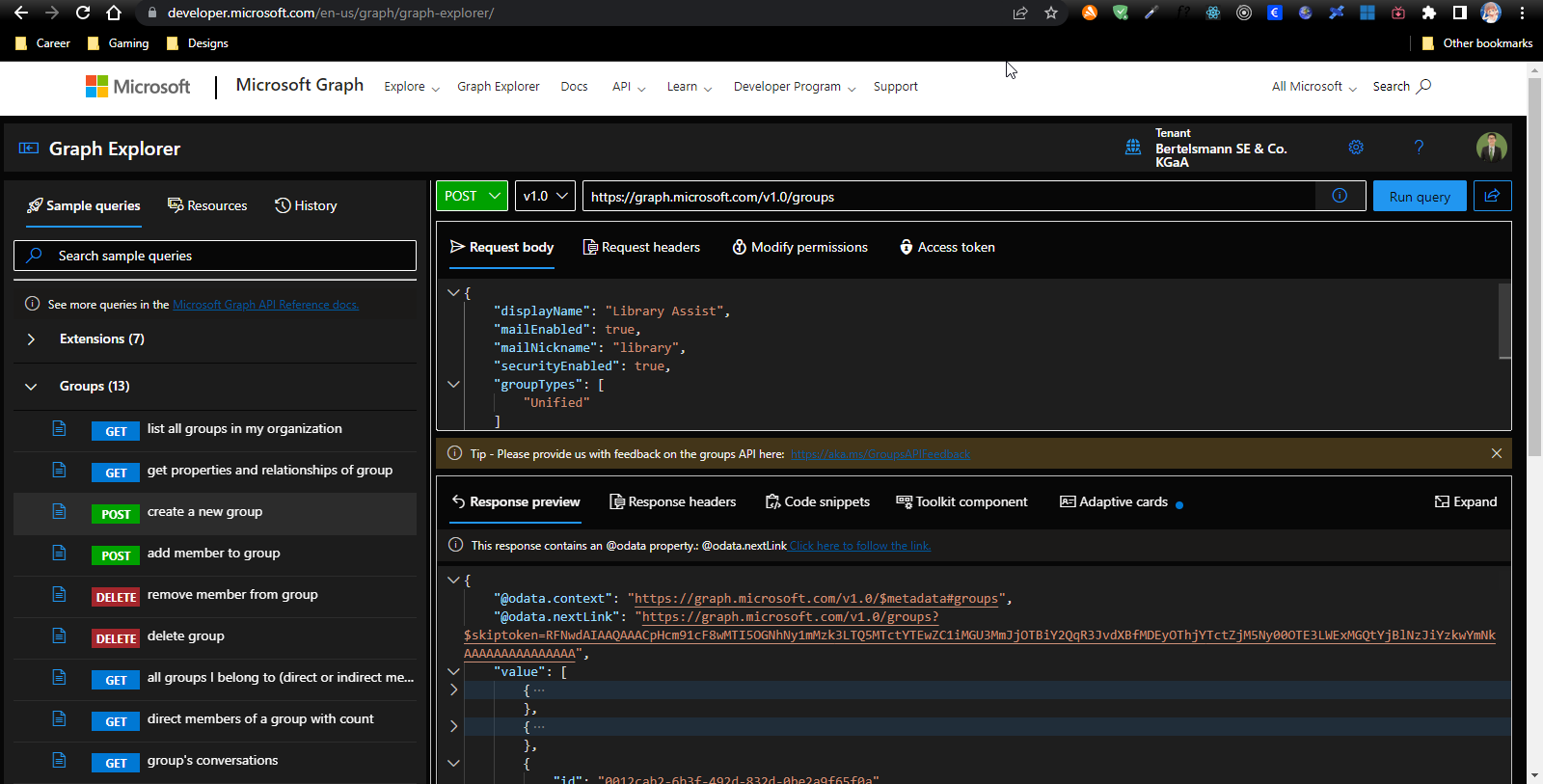
Client Configuration in Keycloak
The following is the Azure Enterprise App configurations used for Keycloak User Federation usage via client-credentials Authentication Flow:
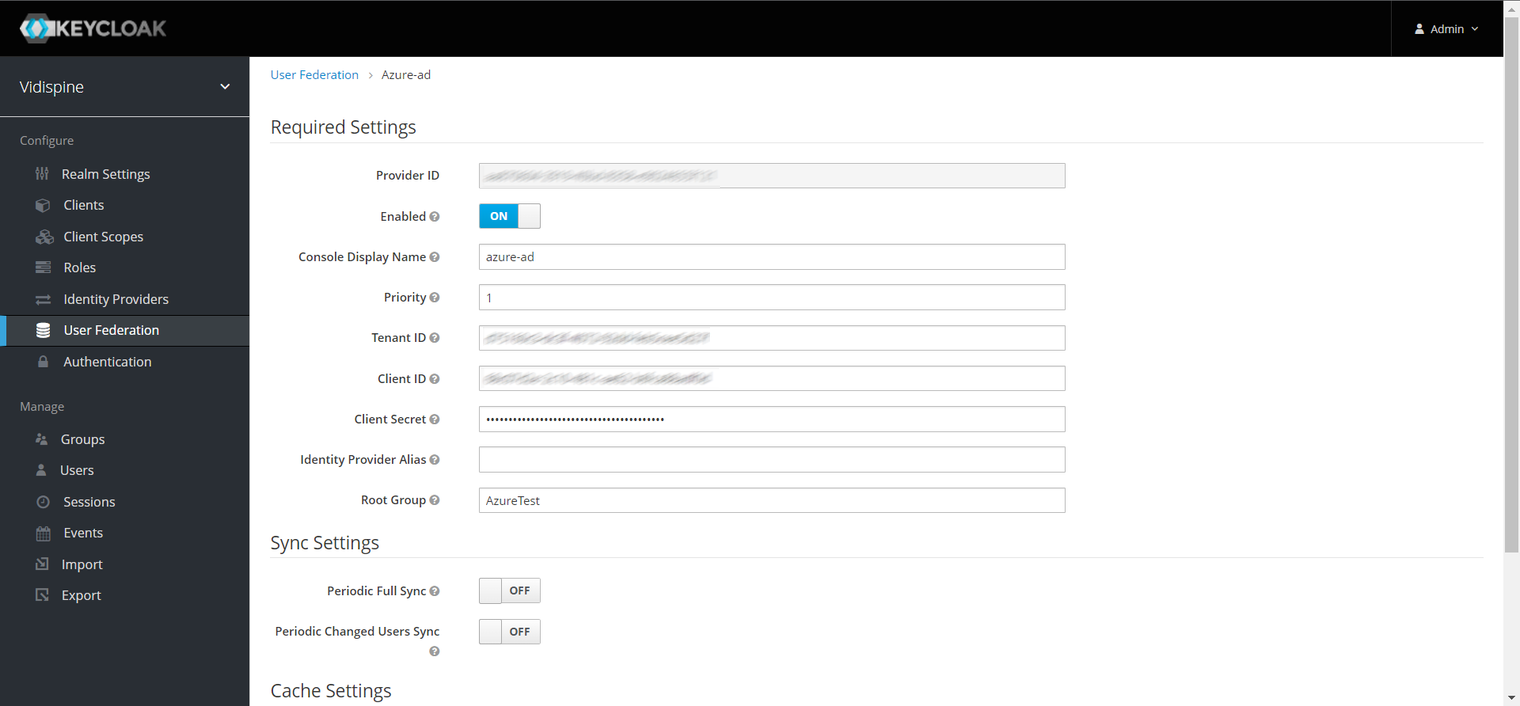

Azure Portal’s Enterprise Application Configuration
Link Login User And User Imported from User Federation
The NameID Policy Format has to set to Email to allow it to auto-link to user imported from the User Federation
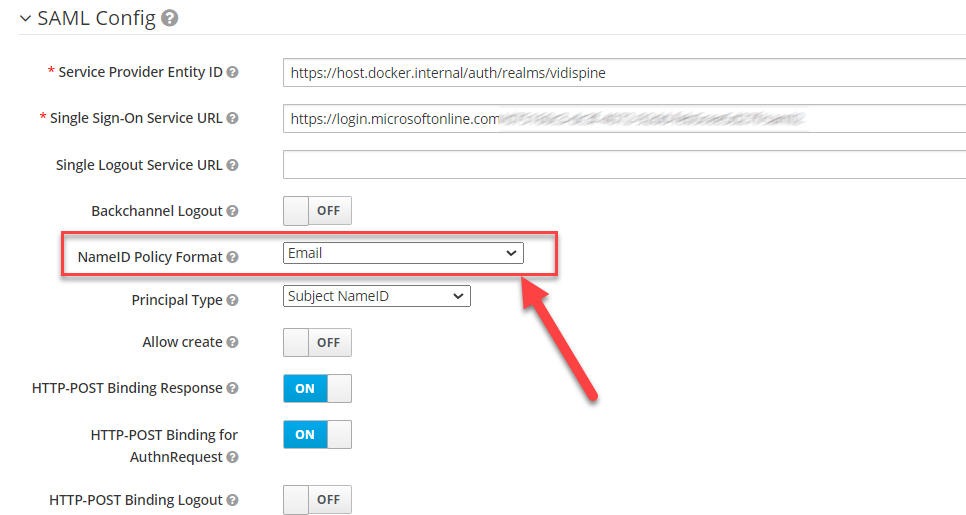
Refer to https://learn.microsoft.com/en-us/azure/active-directory/develop/saml-claims-customization#edit-nameid for NameId Policy
