Microsoft Entra ID / Azure AD integration [C IG]
Overview
The Authorization Service (AS) seamlessly integrates with Microsoft Entra ID (formerly Microsoft Azure AD). Similar to LDAP integration, the AS utilizes Keycloak to synchronize users and groups with Entra ID. The synchronized users and groups are also automatically created within VidiCore.
Configuration is managed through ConfigPortal under the Identity Provider settings. The portal ensures all necessary parameters are correctly configured in Keycloak for smooth operation.
The AS login screen has been enhanced to display a button for logging in with Entra ID when it is enabled. Clicking the button redirects the user to the Entra ID login page, supporting multi-factor authentication if it is configured in Entra ID.
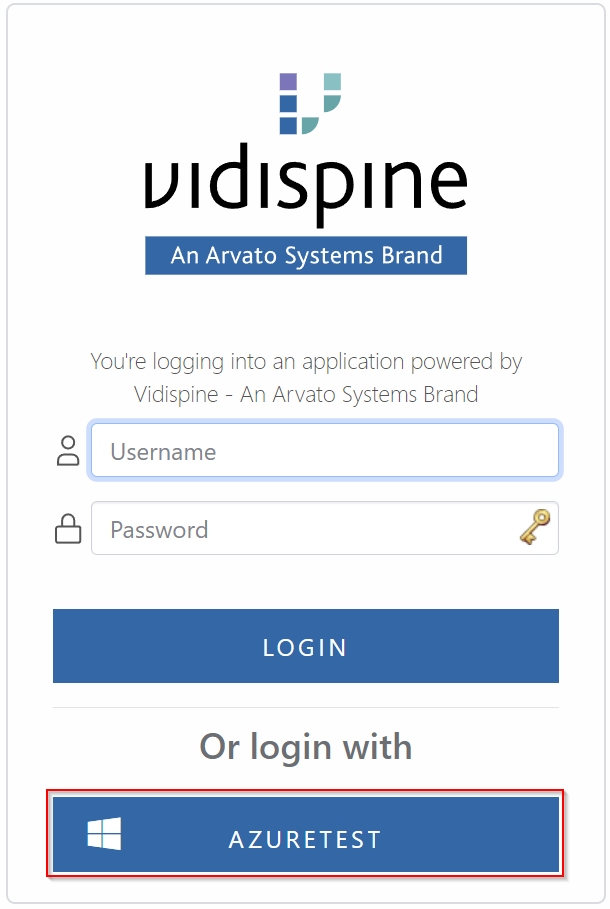
Change AS login screen with Azure AD login button
The Synchronisierung zwischen AAD und KeyCloak findet regelmäßig zeitgesteuert statt.
Configuration
Configuration in Azure Portal
Login
Login into https://portal.azure.com/ with credentials provided in OneNote documentation:
Azure AD Environment 1 (VidiConfig Test System) (Web view)Select “Manage Microsoft Entra ID”
Register New SAML Application
Select “Enterprise applications”
Select “New application”
Search for “Entra SAML Toolkit” and select “Microsoft Entra SAML Toolkit”
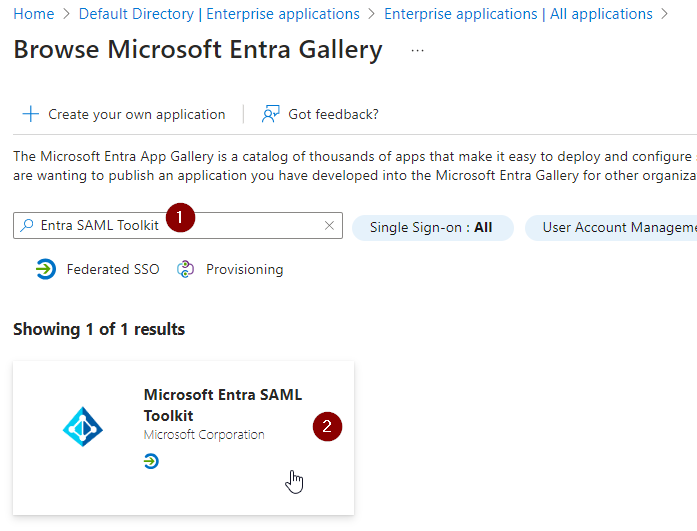
Provide a Name and select “Create”
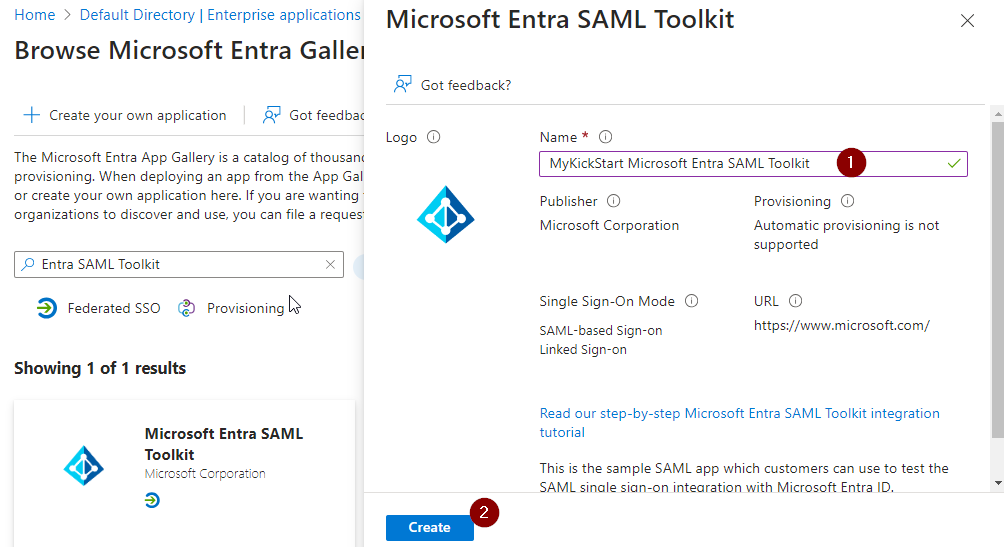
The following link leads to a tutorial to register a new SAML application in Azure AD
https://learn.microsoft.com/en-us/azure/active-directory/saas-apps/saml-toolkit-tutorial
Enable Single sign-on
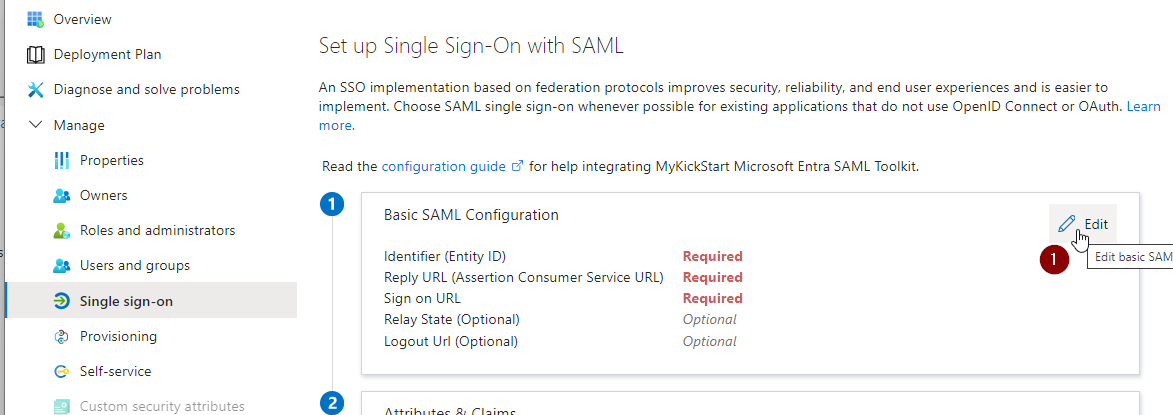
Select “Single sign-on”
Select “SAML”

Edit the “Basic SAML Configuration”
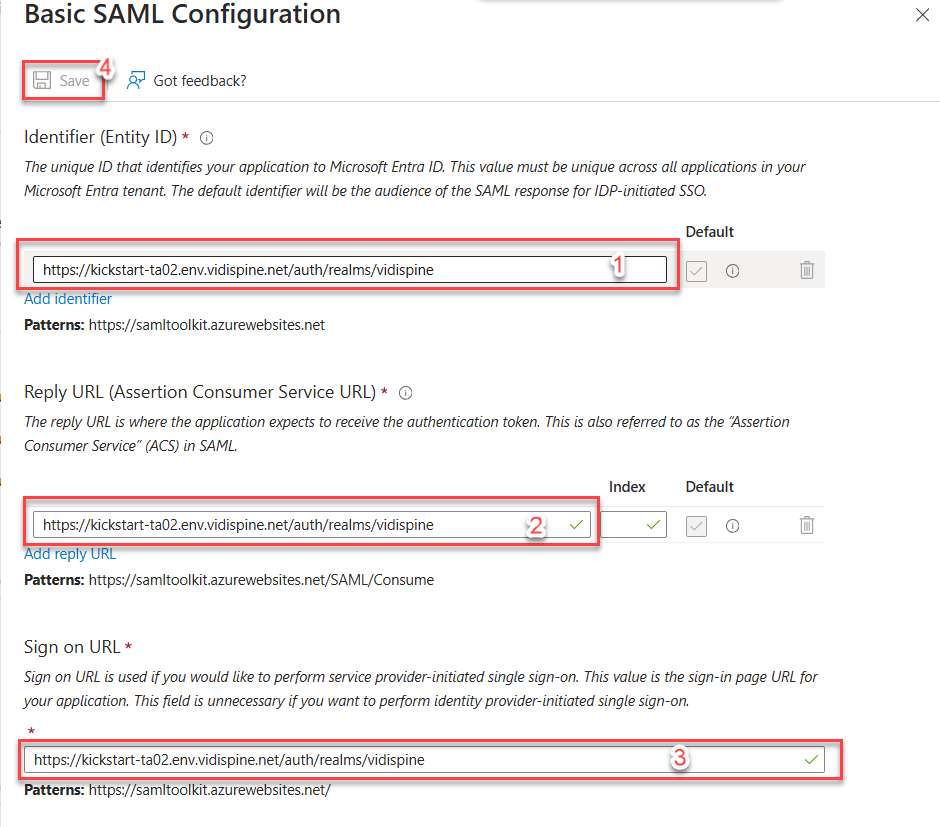
Add
an Identifier
Reply URL:
as URL of the authentication endpoint of your system followed by “/realms/vidispine”, e.g.:
https://kickstartta.env.vidispine.net/auth/realms/vidispineSign on URL:
Same as Reply URLSelect “Save”
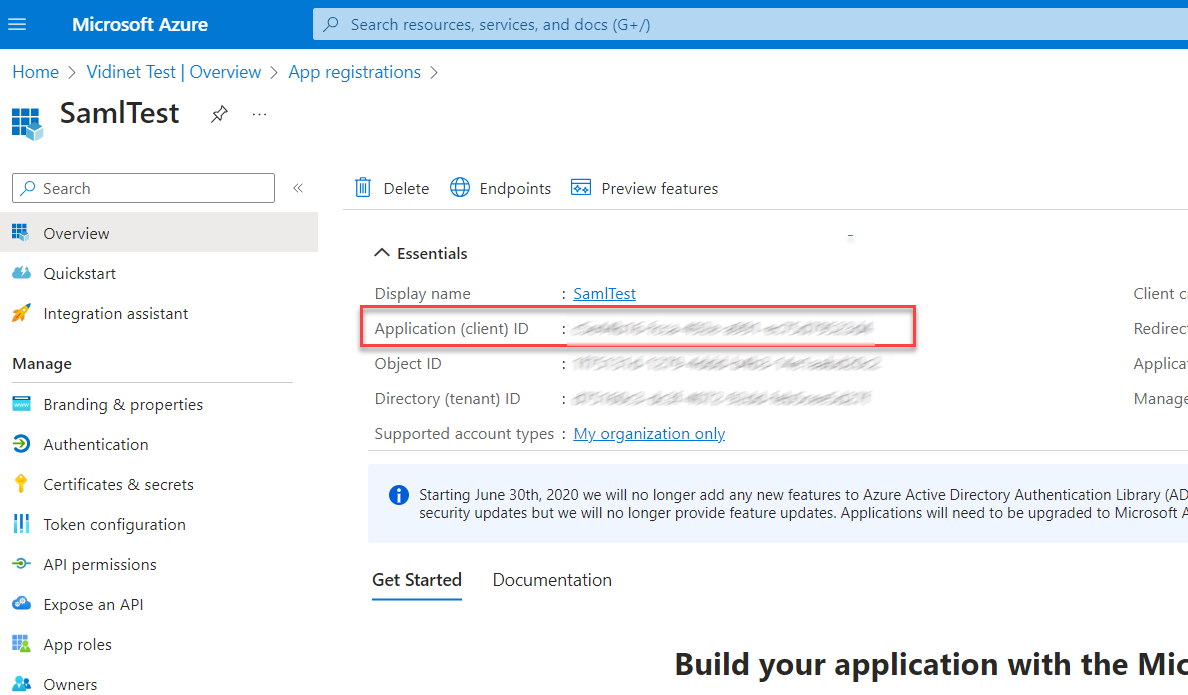
Get Client Id
Get the Client ID from ‘Application (client) ID’
Create Client Secret
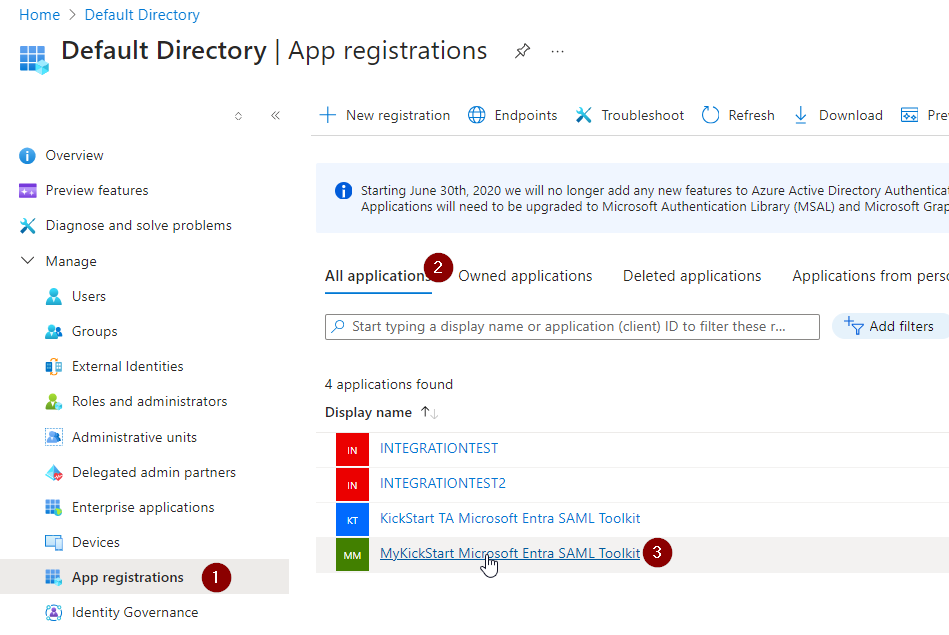
Go back to “Default Directory | Enterprise applications”

Select
“App registrations”
“All applications”
The Name of your created SAML Toolkit
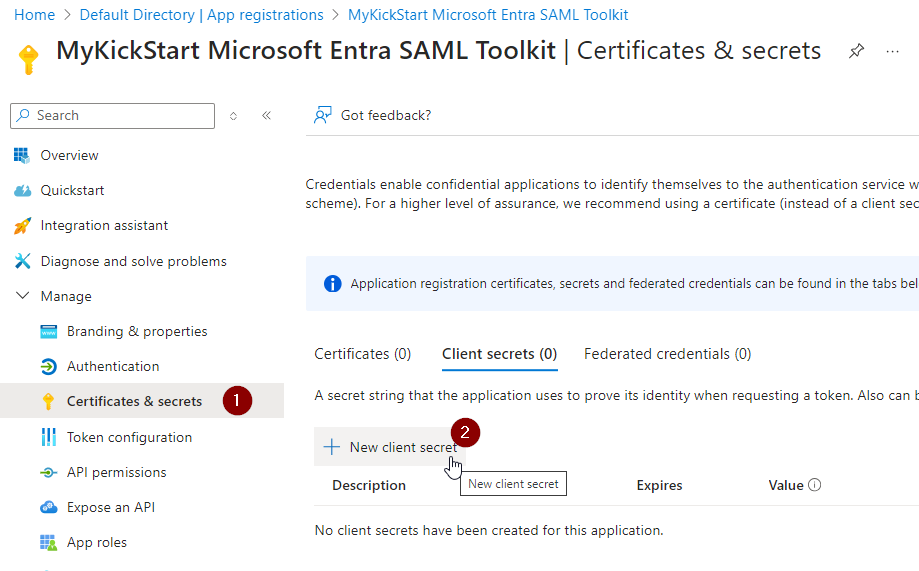
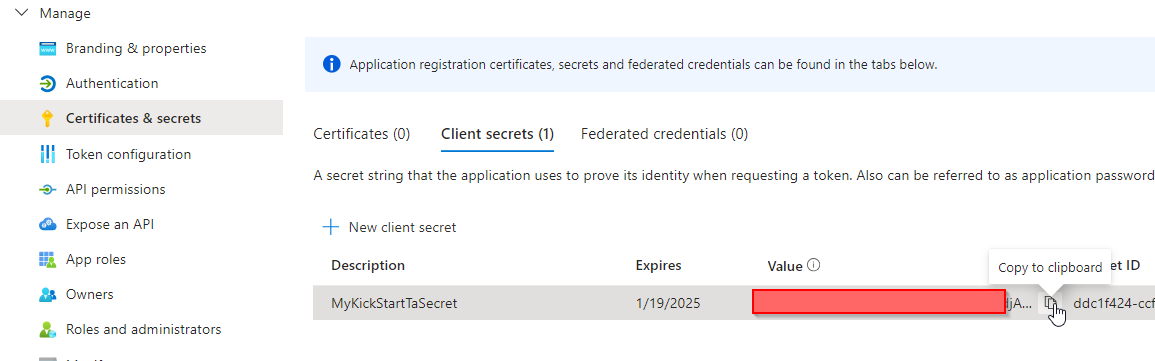
Select “Certificates & secrets” and “New client secret”
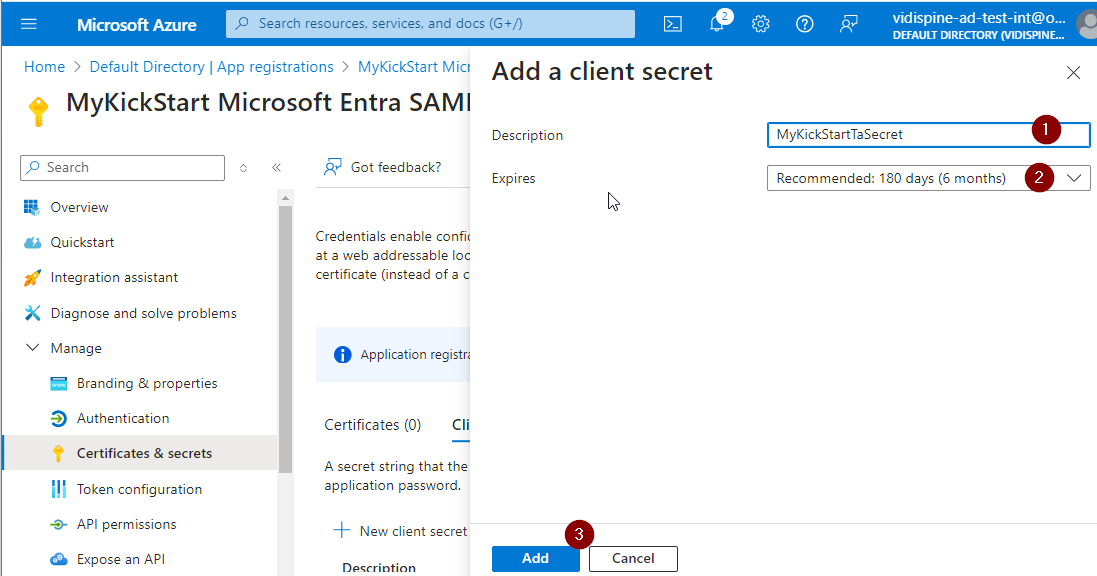
Provide a description and a desired expiration time and select “Add”
Copy value of secret
You must take care to copy the “Value” of the Secret now and save it somewhere for later usage in ConfigPortal.
The value will not be displayed anymore later.
Otherwise you will have to create a new secret for copying the new value and delete the previous one.
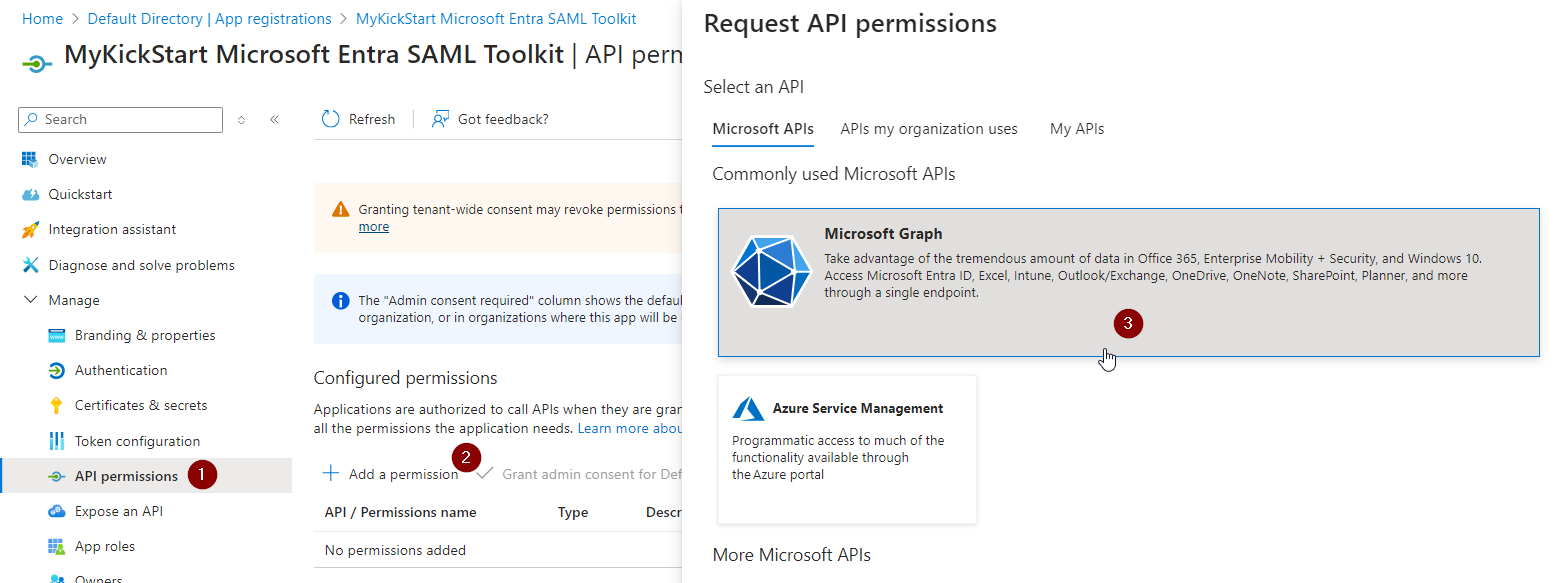
Add API Permissions
When registering the client within Azure Enterprise Applications, the following permissions are required by Keycloak’s Entra ID Provider plugin to be able to federate users and sync locally:
Group.Read.All
GroupMember.Read.All
User.Read.All
To do so proceed as follows
Select
“API permissions”
“Add a permission”
“Microsoft Graph”
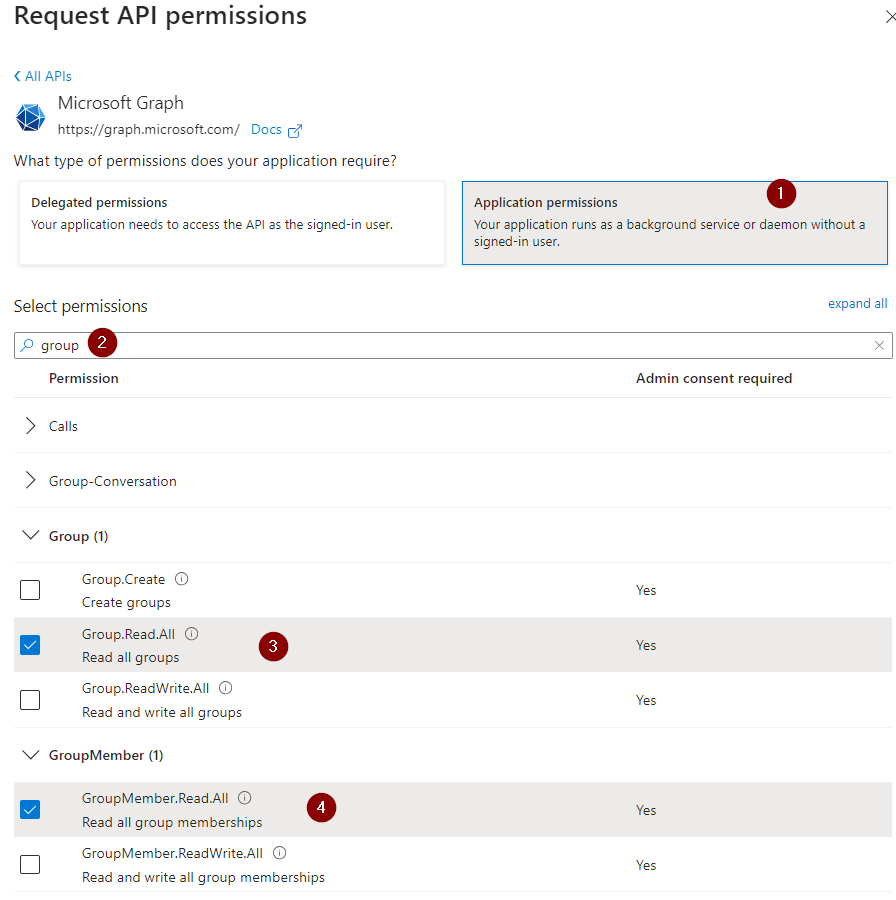
Select “Application permissions”
Activate
Group.Read.All
GroupMember.Read.All
User.Read.All
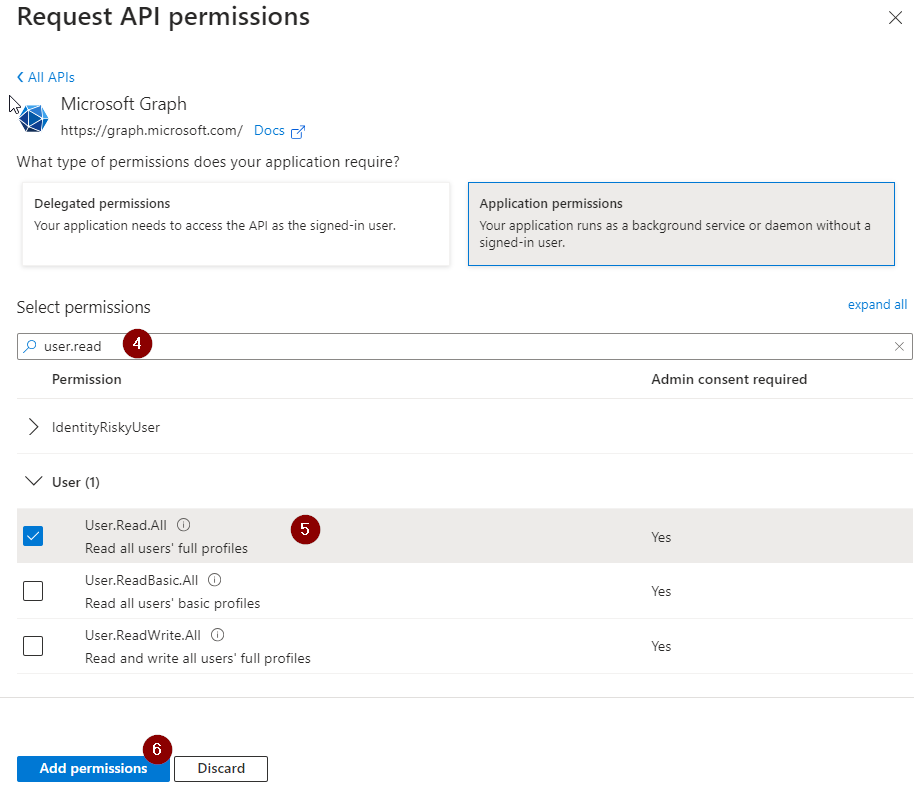
Select “Add Permissions”
Grant admin consent
Important:
You will see warnings “Not granted fror Default …”
To solve that please
Select “Grant admin consent for Default Directory”
Select “Yes”
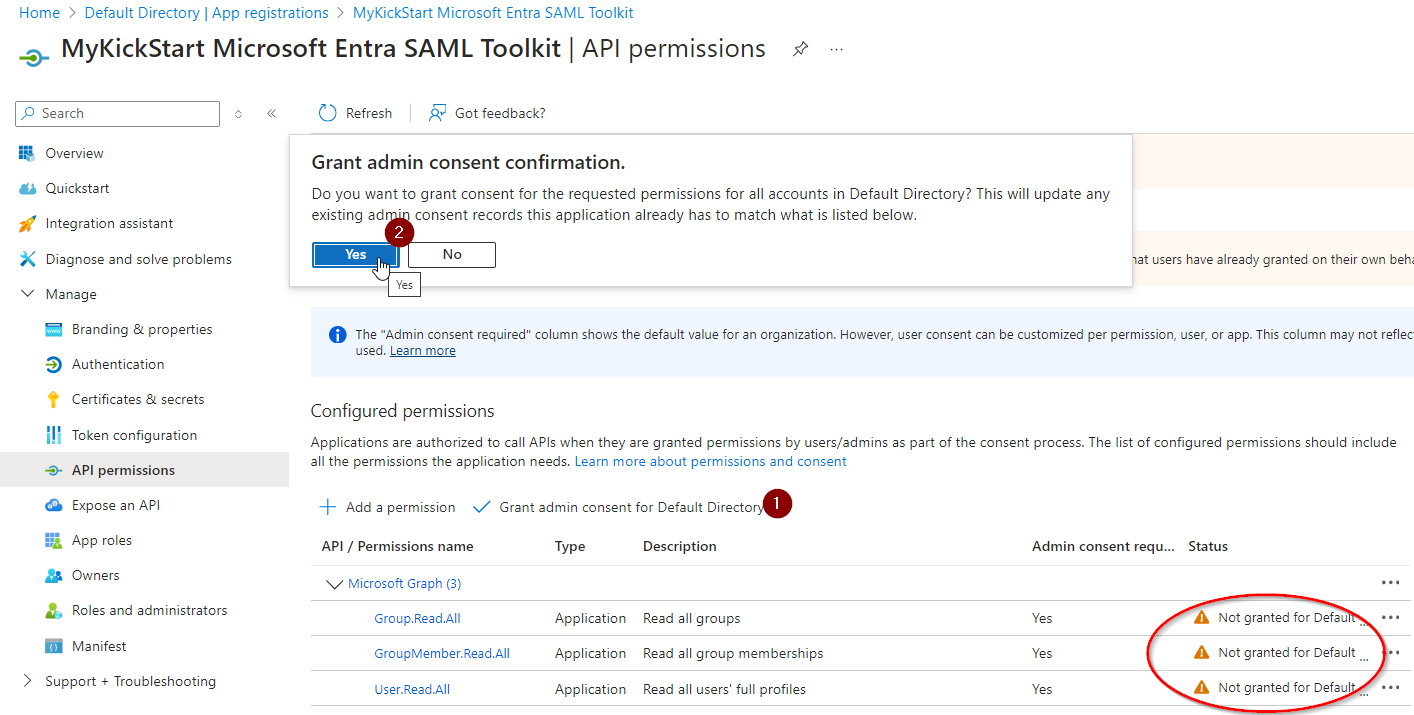
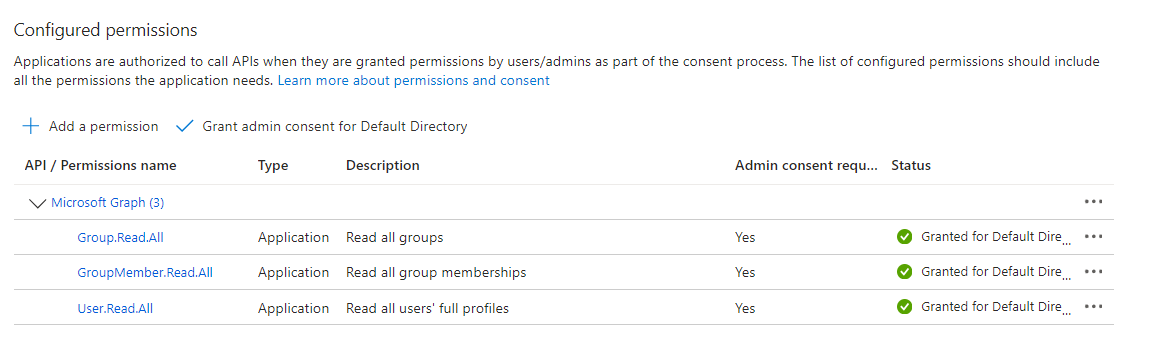
No all should be “green”
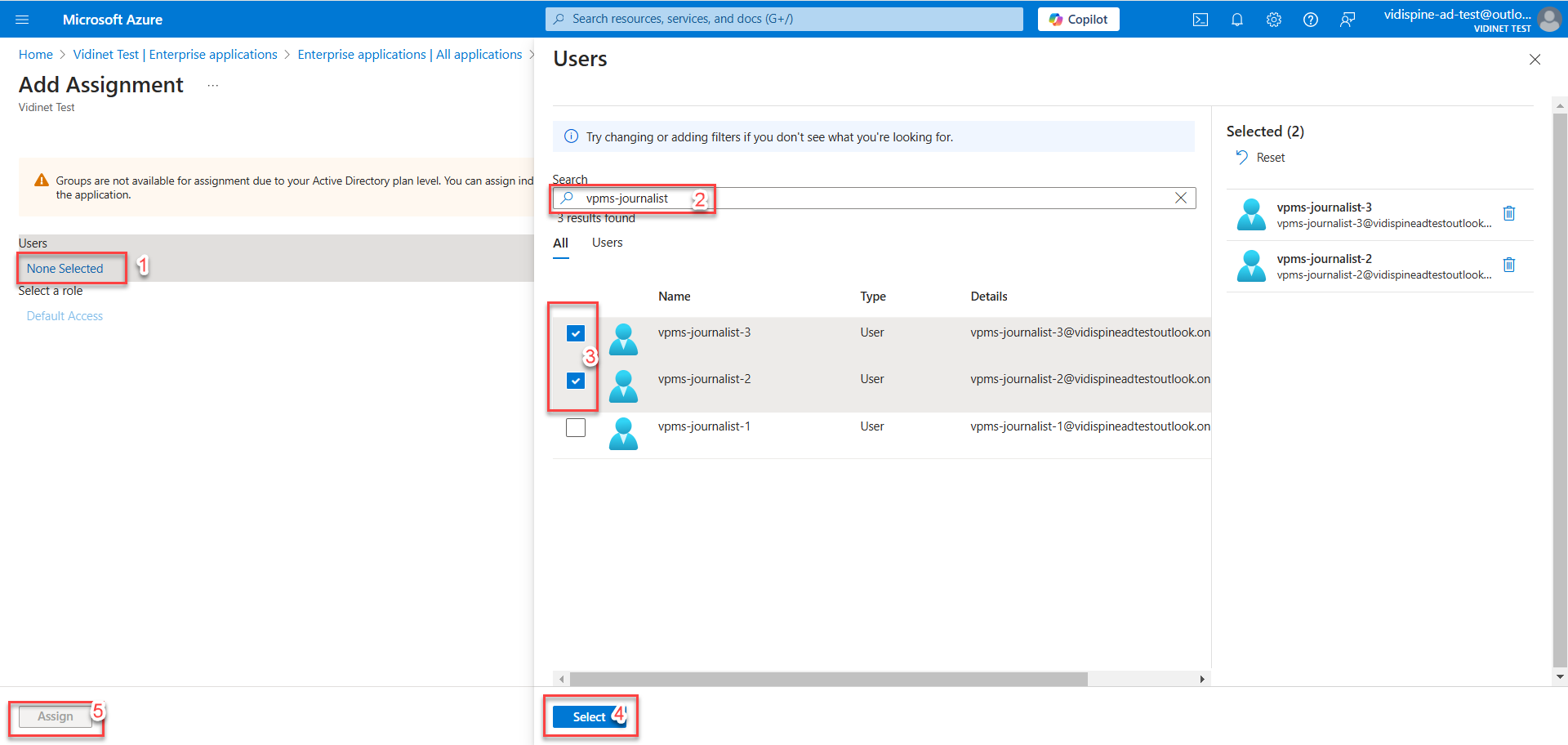
Assign Users to Application
To enable the created users to log in to the application, they must be assigned to it.
Select “Enterprise applications”

Select the created application
Click “Assign users and groups”

Click “Add user/group”
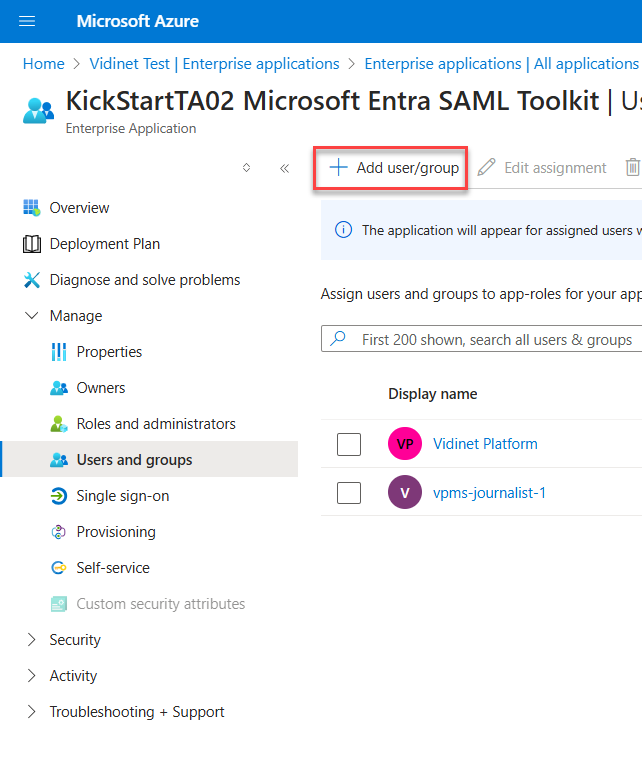
Click on 'None Selected' to search for users to assign to the application. Check the desired users and click 'Select'. Finally, click 'Assign' to complete the process.
Configuration in ConfigPortal
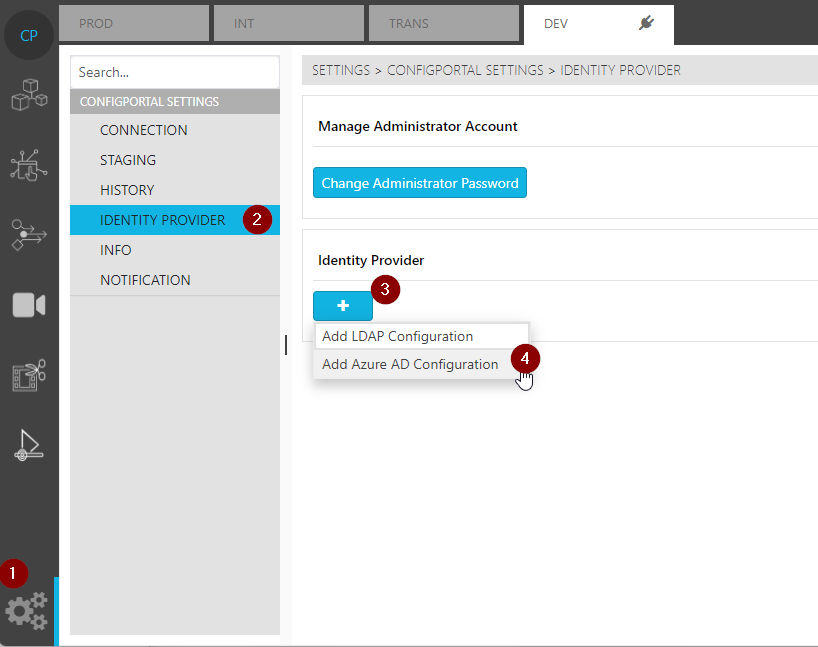
Now you will have to configure the Entra ID account as identity provider in ConfigPortal as follows.
Open ConfigPortal on corresponding system
Select
“Settings”
“Identity Provider”
Add button
“Add Azure AD Configuration”
Configuration Parameters
Provide following parameters
Alias Name
SAML Config:
Please retrieve it from Azure Portal like follows: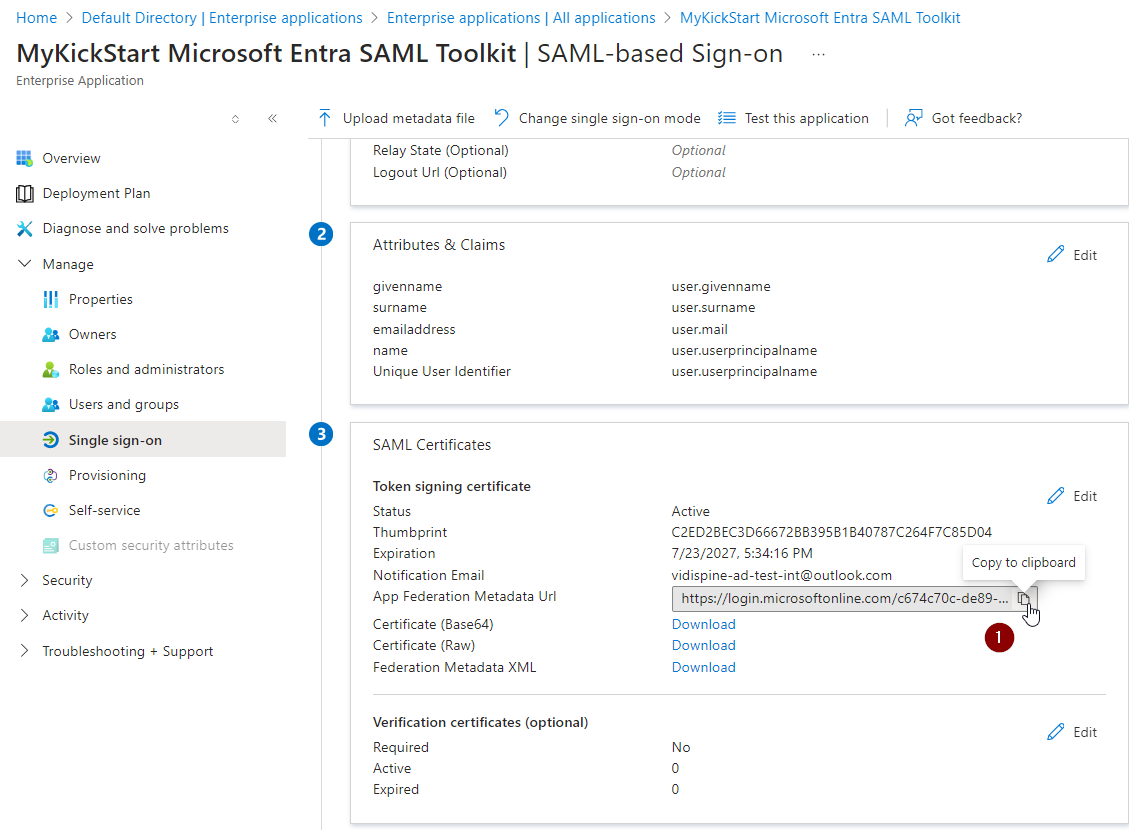
Tenant ID, Client ID: can be copied form Azure Portal

For client secret use the value you copied in https://vidispine.atlassian.net/wiki/spaces/IKBVNKS/pages/3107815427/Identity+Provider+VNKS#Creation-of-Certificate-and-Client-Secret , step 5
Select “Save”
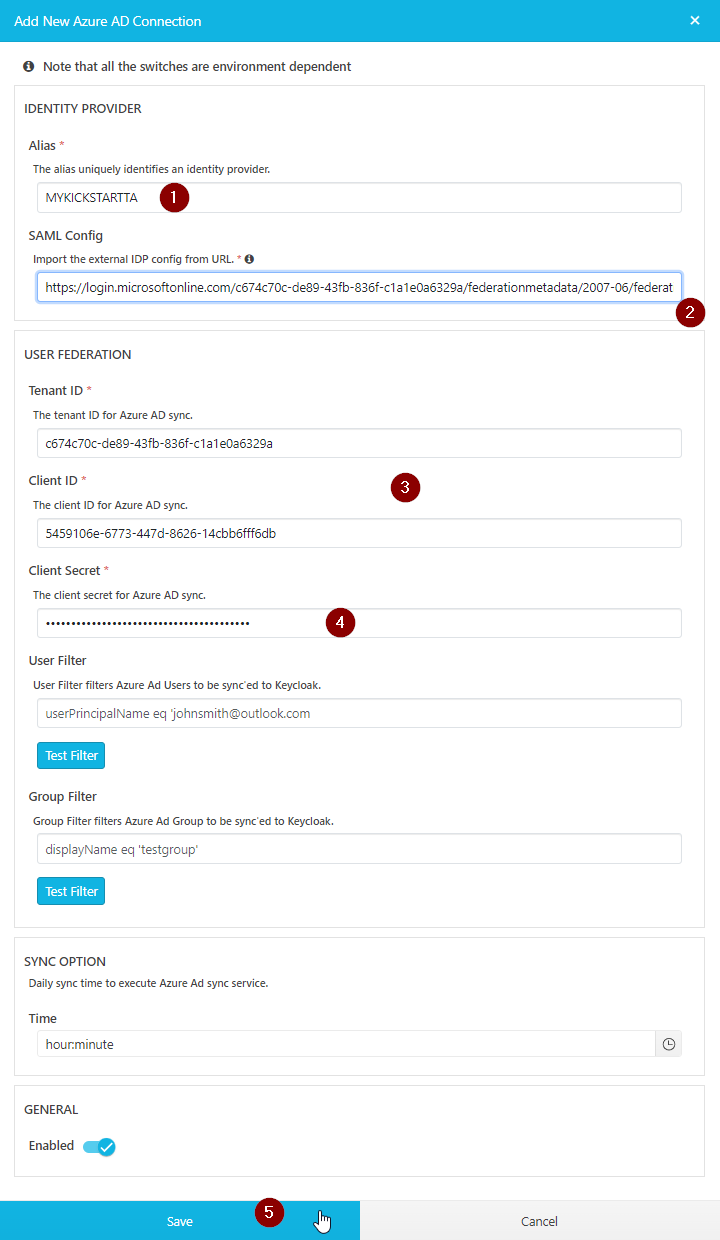
The “Group Filter” allows to whitelist groups. Only users being member of at least on of these groups will be synched to KeyCloak and VidiCore. This feature can help to reduce the amound of users to be synched and for that reason speed up the synch prozess a lot.
Be aware that this feature will be enhanced in the future, probably without migration of the existing configuration.
Sync Users and Groups
Now you should be able to sync all users and groups from configured Entra ID
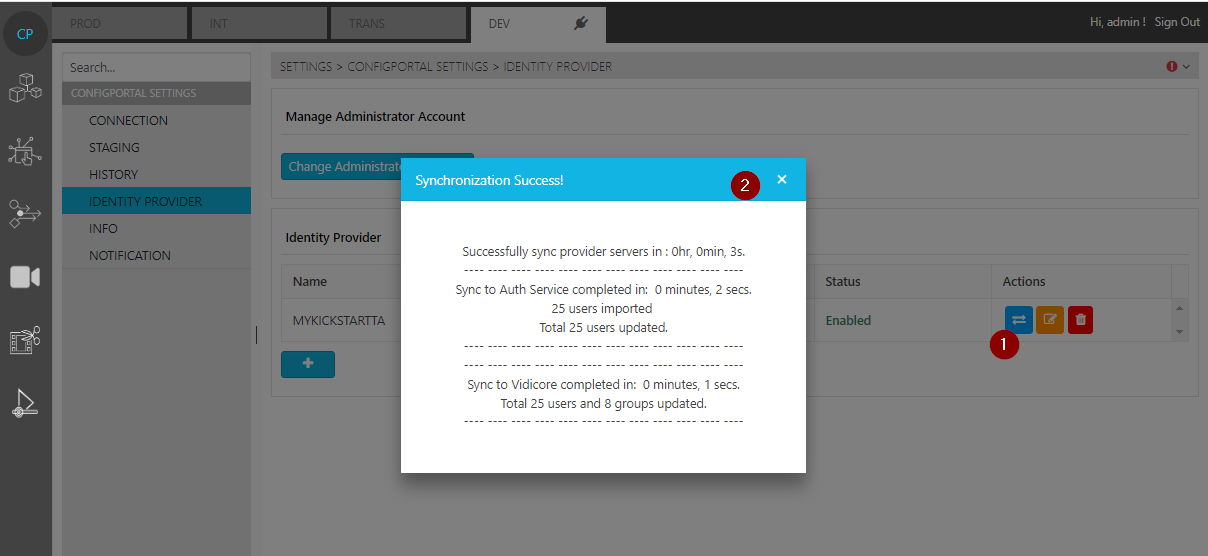
Technical detail information
Microsoft Graph API
Microsoft Graph API is used for most of our enterprise app usages for retrieving data for user federation purpose in Keycloak.
Rest API: https://developer.microsoft.com/en-us/graph/graph-explorer/
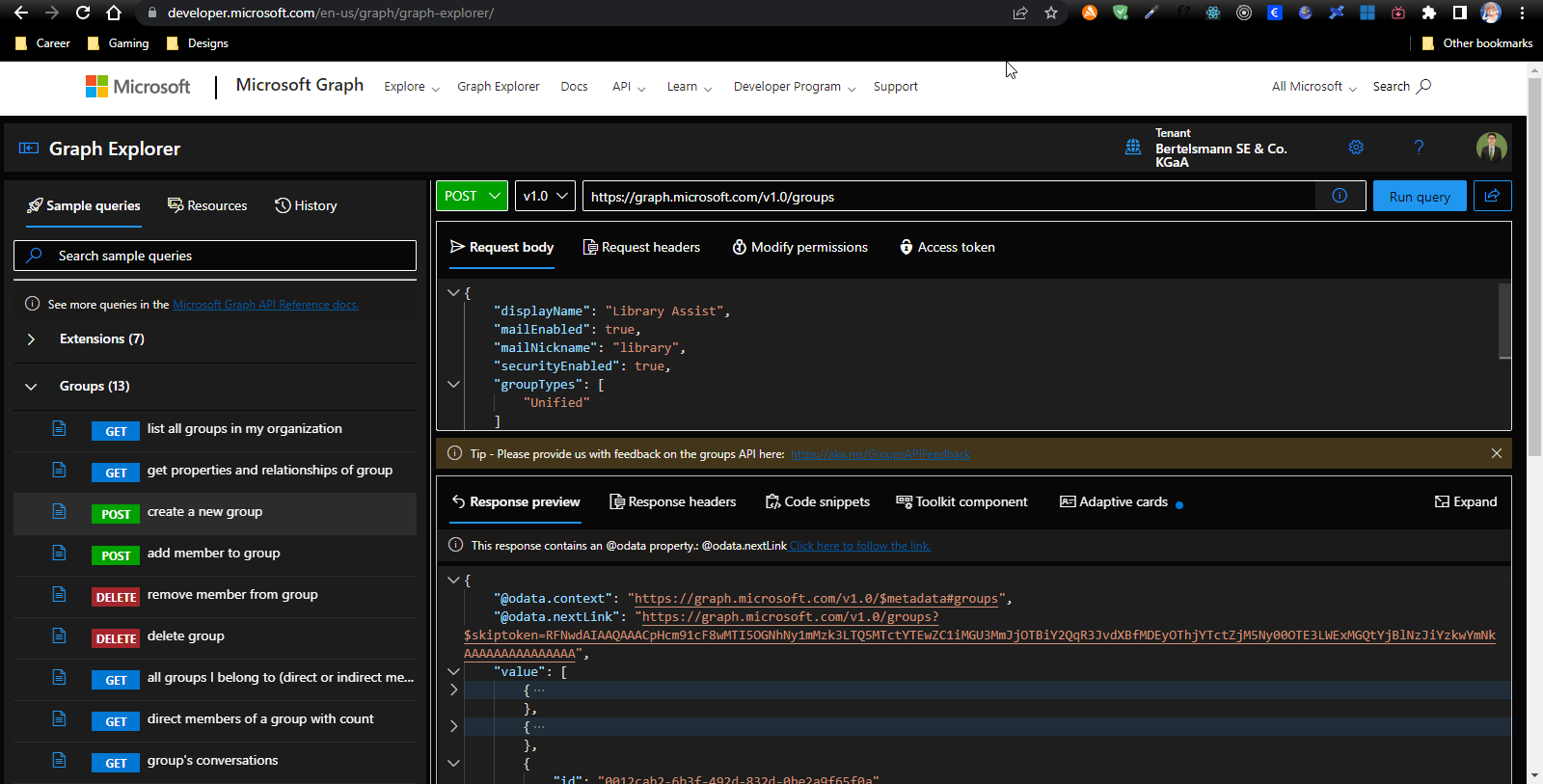
Client Configuration in Keycloak
The following is the Azure Enterprise App configurations used for Keycloak User Federation usage via client-credentials Authentication Flow:
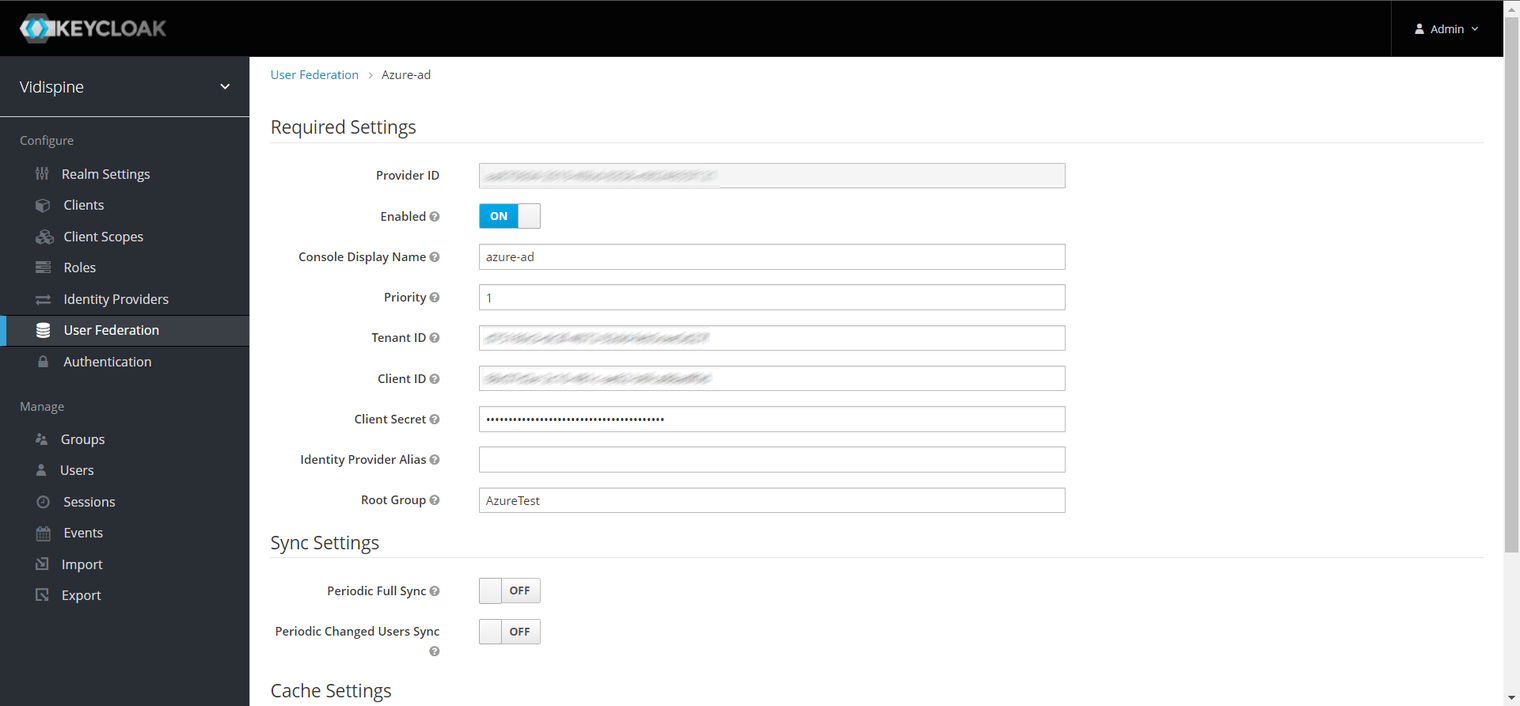

Azure Portal’s Enterprise Application Configuration
Link Login User And User Imported from User Federation
The NameID Policy Format has to set to Email to allow it to auto-link to user imported from the User Federation
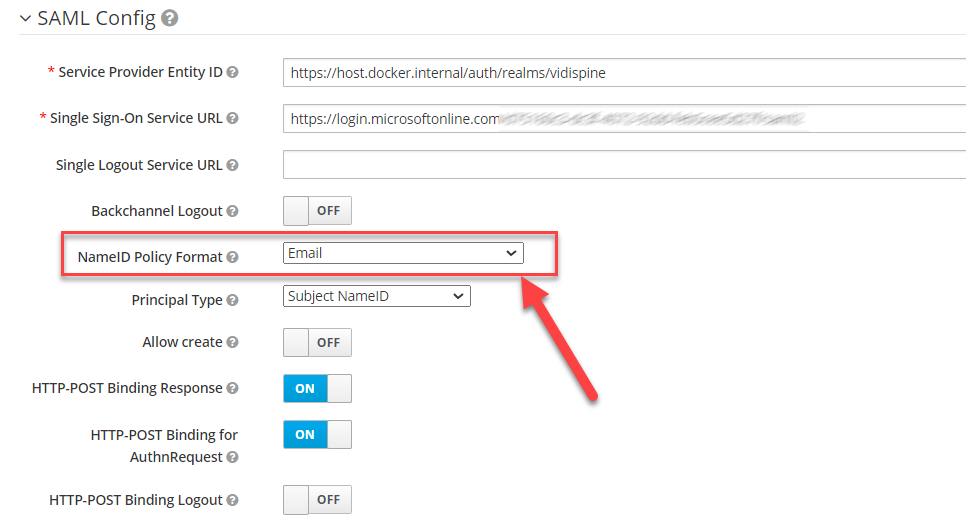
Refer to https://learn.microsoft.com/en-us/azure/active-directory/develop/saml-claims-customization#edit-nameid for NameId Policy
